Active Computers & Programming Posts


How To: Set up two monitors on one computer
This video will show you how to connect two monitors to one computer for more work space and comfortability.
How To: Use & enable Windows Remote Desktop
Sometimes shit goes down on your home computer and you're just not able to be home to fix it. After all, most of us have commitments such as school, work, and volunteer activities that keep us away from our home computers for most of the day.

How To: Build a movie server to complete your video jukebox
Get an inside on how to build a home server that hosts all of your DVDs and movie content.

How To: Burn CDs/DVDs
Tinkernut shows you how to burn CD and DVD copies. Infrarecorder is a program that lets you record music/data/mixed CD's, DVD's and dual layer DVD's.
How To: Install dual operating systems like Linux, XP, OSX etc
Installing two operating systems and then dual boot your machine. This is to put more than just Windows and Linux and OSX on the same machine. Another option is a virtual desktop option. This video will guide you through the steps of setting your computer up to boot two different operating systems.

How To: Control your computer with a webcam & Wii remote
This is a Tinkernut video cast. This video shows you how to control your computer (mainly games and miscellaneous programs such as Google Earth) using your webcam.
How To: Defragment your computer while idle
This video shows you how to set up a scheduled task to run anytime your computer is idle that defragments your computer. Defragmenting is important because it will allow your programs to open much faster.

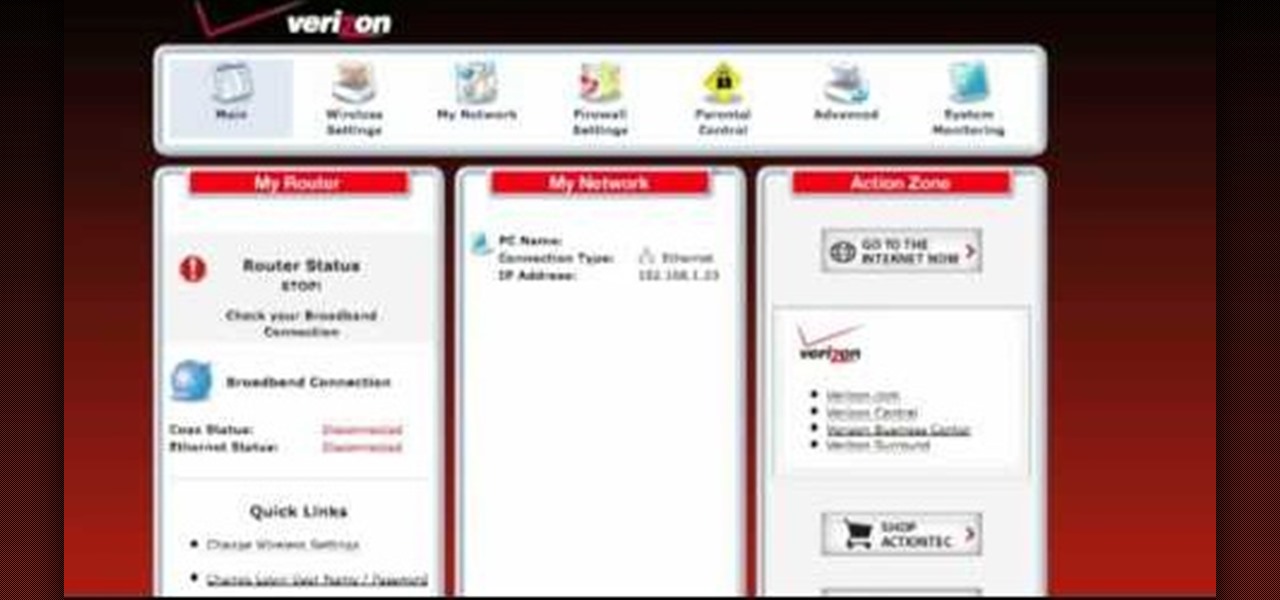
How To: Set up and install the Verizon MI424WR FiOS Router
Learn how to set up and install the Verizon MI424WR FiOS Router. This video tutorial will show you the easy steps to installing and setting up the Verizon FiOS Router by Actiontec Electronics.

How To: Take a screen capture with the Snip tool in Vista
Need to capture an image from your desktop? Learn how to use the snipping tool in Windows Vista, and you can grab an image from anywhere on your computer screen.

How To: Convert a Visual Basic project to Jabaco Java
In this video tutorial / demonstration you will learn how to convert an existing Visual Basic project to Jabaco Java. You will need both Microsoft Visual Basic and Jabaco, a simple programming language with a Visual Basic like syntax. Jabaco enables you to create powerful software for all Java supported operating systems. Convert a Visual Basic project to Jabaco Java.

How To: Control an LED with Arduino
See how to control an LED with Arduino with MAKE Magazine! This is a video tutorial on a favorite little micro-controller, the Arduino. This is a really informal how-to, and is meant to show you just how fast and easy it is to work with the Arduino.

How To: Connect your Mac to your XBox 360 with Connect360
Interested in connecting your Apple computer to your XBox 360 game console? In this how-to, Gary Rosenzweig looks at how you can use your XBox 360 to view video and listen to music that is stored on your Mac using Connect360.

How To: Modify the Windows XP boot screen
A quick visual tutorial on how to change the boot screen dialogue on any Windows XP machine. Great for messing wtih friends.

How To: Add memory to a Apple MacBook Pro notebook computer
Learn how to add memory (RAM) to a Apple MacBook Pro notebook computer. Upgrading your MacBook Pro laptop memory is easy to do and an inexpensive way to improve the performance of your MacBook.

How To: Install memory in a Compaq Presario laptop
Learn how to upgrade your RAM memory for a typical laptop or notebook computer. In this example, we show you how to install memory in a Compaq Presario laptop. Upgrading your laptop memory is easy to do and an inexpensive way to improve the performance of your laptop.

How To: Install memory in a laptop
Learn how to a install memory upgrade in your laptop computer. Simple to do instructions when upgrading your notebook with new RAM. This video tutorial is from EDGE Tech Corp.
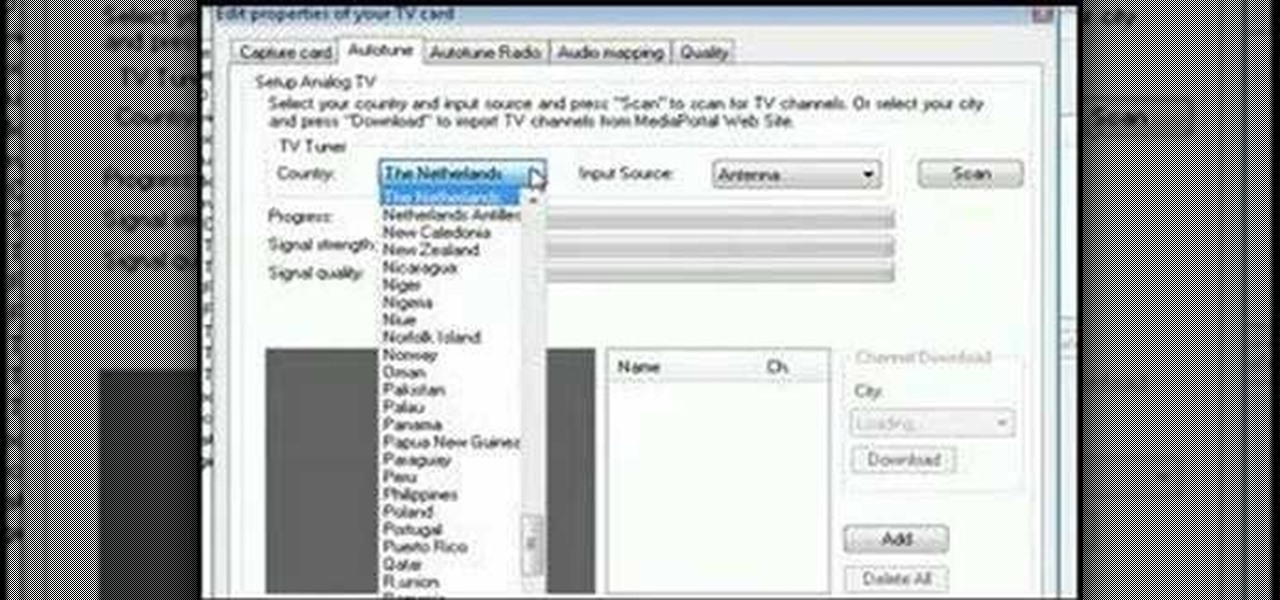
How To: Make a DVR from an old computer
Turn an old computer into a DVR that you can use to watch TV and record shows from over the internet using a TV card and free software.

How To: Improve wireless networking on Verizon's FiOS Router
Learn how to improve wireless networking on Verizon's FiOS Router. You'll see some easy tips on how to improve wireless networking with the MI424WR Verizon FiOS Router, by Actiontec.
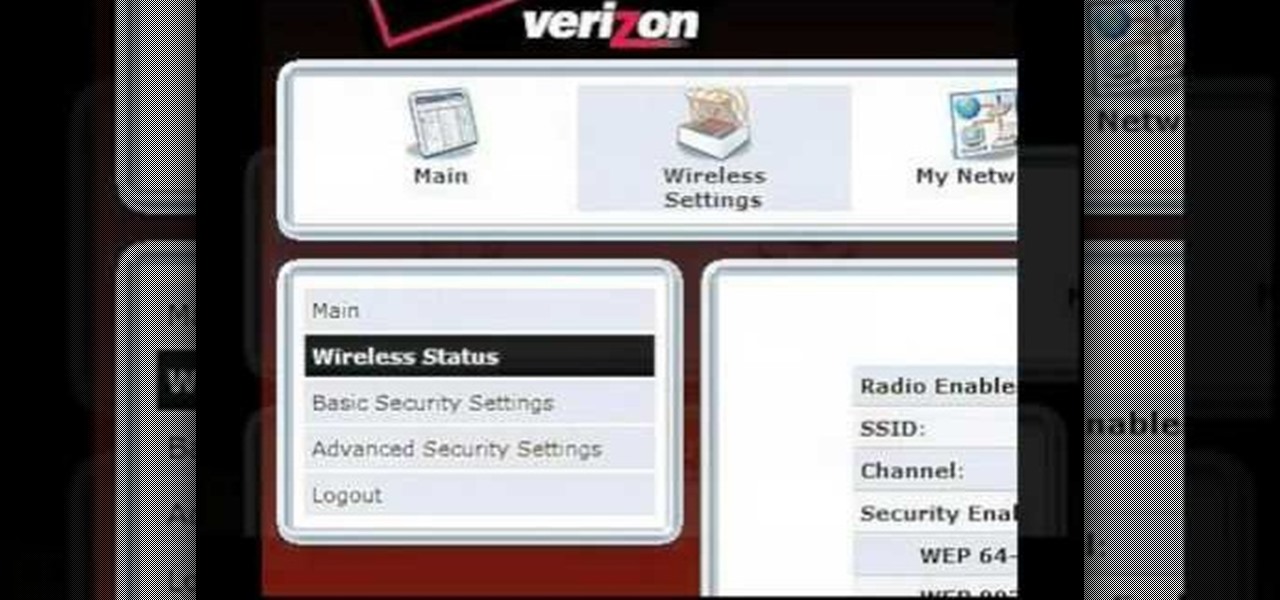
How To: Change a wireless network name Verizon's FiOS Router
Learn how to change your wireless network name on Verizon's FiOS Router. You'll see the easy steps on how to change your wireless network name and / or password for your MI424WR Verizon FiOS Router, manufactured by Actiontec Electronics, Inc.

How To: Find a username and password on a Verizon FiOS Router
Learn how to determine username and password on a Verizon FiOS Router. You'll see the easy steps on how to find out or reset the user name and password of your Verizon FiOS Router by Actiontec.

How To: Convert an old PC into a home audio server
Do you have an old PC sitting around somewhere in your garage? Want a dedicated audio server that will play back MP3s, Internet radio, and other digital music files over your home stereo system? This CNET video teaches you how to convert your old PC into an amazing server!
How To: Create rounded corners for boxes on a CSS website
Here are five different techniques you can use to create rounded corners for boxes on a website. There are always different ways to do things with CSS and rounded corners is a great example of that. Each of these five techniques has advantages and disadvantages. Knowing all of them so you can choose the perfect one in each situation is the kind of thing that makes you the best CSS ninja you can be! So if you want to make cool Internet websites and be the best designer around, why not start he...

How To: Improve video search by parsing video & text
This is a Google Tech Talk from March, 26 2008. Timothee Cour - Research Scientist lectures. Movies and TV are a rich source of highly diverse and complex video of people, objects, actions and locales "in the wild". Harvesting automatically labeled sequences of actions from video would enable creation of large-scale and highly-varied datasets. To enable such collection, we focus on the task of recovering scene structure in movies and TV series for object/person tracking and action retrieval. ...
How To: Setup basic port forwarding for a Verizon FiOS Router
This video explains how to set up port forwarding on the Verizon MI424WR router. See how to setup basic port forwarding for a Verizon FiOS Router.

How To: Configure advanced port forwarding on a MI424WR Router
This video will explain how to set up advanced port forwarding on the Verizon MI424WR router. See how to configure advanced port forwarding on a MI424WR Router.

How To: Setup the Verizon FiOS Router for multiplayer gaming
Learn how to setup the Verizon FiOS Router for multiplayer gaming. Most games and gaming consoles only require that UPnP (Universal Plug-n-Play) be turned on. The MI424WR Verizon FiOS Router that is manufactured by Actiontec ships with UPnP ON, as the default.

How To: Refill an ink cartridge
If you use your inkjet printer regularly, you’ve probably discovered that the cost of replacing the cartridges can quickly exceed that the printer itself. Refill the cartridges yourself to save some money.

How To: Convert MKV to M4V video format
This is a shot how to tutorial on how to convert those HD mkv files you download from the web to a m4v file format. This way you will be able to play those files natively in HD on your Microsoft XBOX 360 and AppleTV.
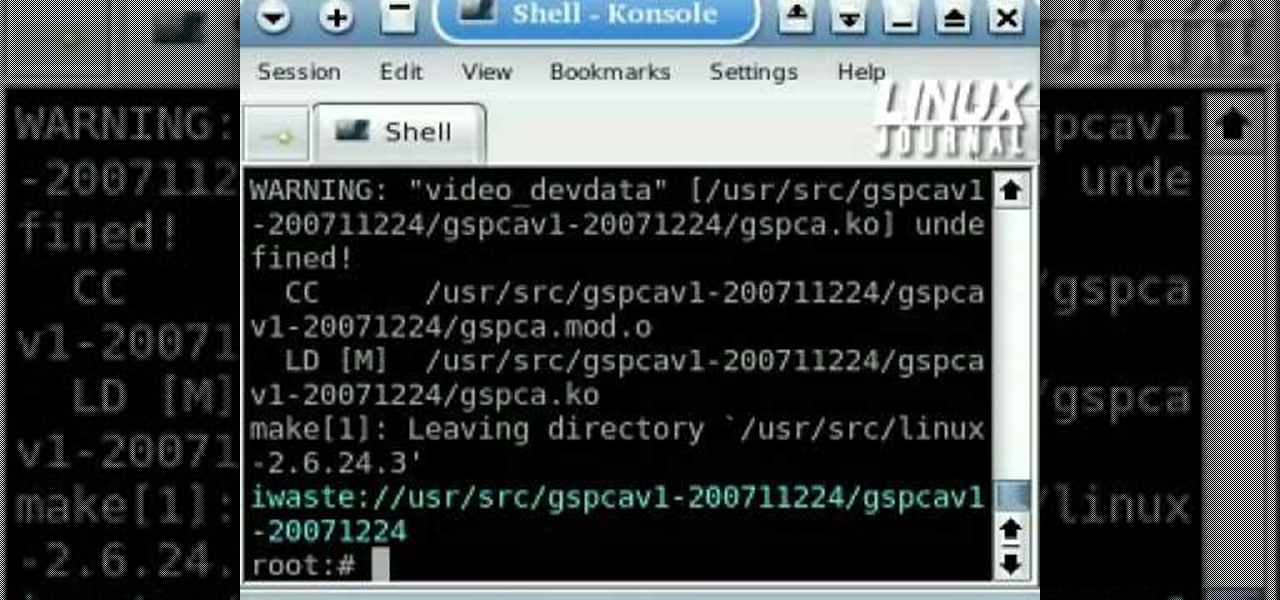
How To: Get your webcam working under Linux with GSPCA
Webcams are notorious for their lack of support under Linux. But thanks to GSPCA, many webcams now have functional V4L drivers. This tutorial from Linux Journal Online covers the building, installation, and configuration of the GSPCA drivers, including how to adjust color balance and brightness directly at the kernel module level.
How To: Display the current time in a VB.Net program
In this tutorial teaches you how to add the current time on a VB.Net project

How To: Install your 2Wire Gateway for High-Speed Internet
Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing your 2Wire Gateway for EMBARQ High-Speed Internet. This will cover exactly how to install your EMBARQ 2Wire Gateway modem for Internet. This is the complete process step-by-step from box to connected online.

How To: Install your EMBARQ Modem for High-Speed Internet
Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing your EMBARQ 660 Modem. This will cover exactly how to install your EMBARQ Modem for EMBARQ High Speed Internet service. This is the complete process step-by-step from box to connected online.

How To: Connect to your 2Wire Gateway via wireless Internet
Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on configuring and connecting to your 2Wire Gateway via DSL wireless Internet instead of through an Ethernet cable. make sure to follow this whole process to get your High-Speed Internet up and running on your computer.

How To: Install DSL 2Wire Gateway filters on home phones
Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing DSL 2Wire Gateway filters on home phones. Make sure to repeat the install process for the Gateway filters for each telephone in your house that uses the same phone number as your High-Speed Internet.

How To: Use the Hacker Defender rootkit or HackDef
Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...

How To: See who is connected to a computer with netstat
Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

How To: Enable the Vista Aero theme in Windows Server 2008
People are very opinionated about what version of Microsoft they like. Some people love the easy-to-use nature of classic Windows 2000 and stick with that, whereas others love the upgraded, super sleek Windows Vista version which has its faults but at least looks amazing.

How To: Overlay HTML controls on Silverlight content
In this video tutorial, which highlights Silverlight's flexibility, you will learn how to overlay HTML controls on Microsoft Silverlight content using the Silverlight windowless mode. (You can also use ASP.NET controls in a similar manner of your page is a .aspx page.)

How To: Record and capture audio from any video in Windows
Learn how to record audio from video files (even Flash .flv files or Youtube videos) using the Windows sound recorder. All of the software used in this tutorial comes bundled with Windows.

How To: Protect your computer from snoops
Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.